Table of Contents
Platforms managing financial data cannot verify transaction sources manually. Audit trail compliance requires structured records that show when data was accessed, where it came from, and who authorised it.
Key Takeaways
What problem does this solve?
Platforms cannot reliably track financial data origin or maintain proper consent records for compliance checks.
Why does infrastructure matter?
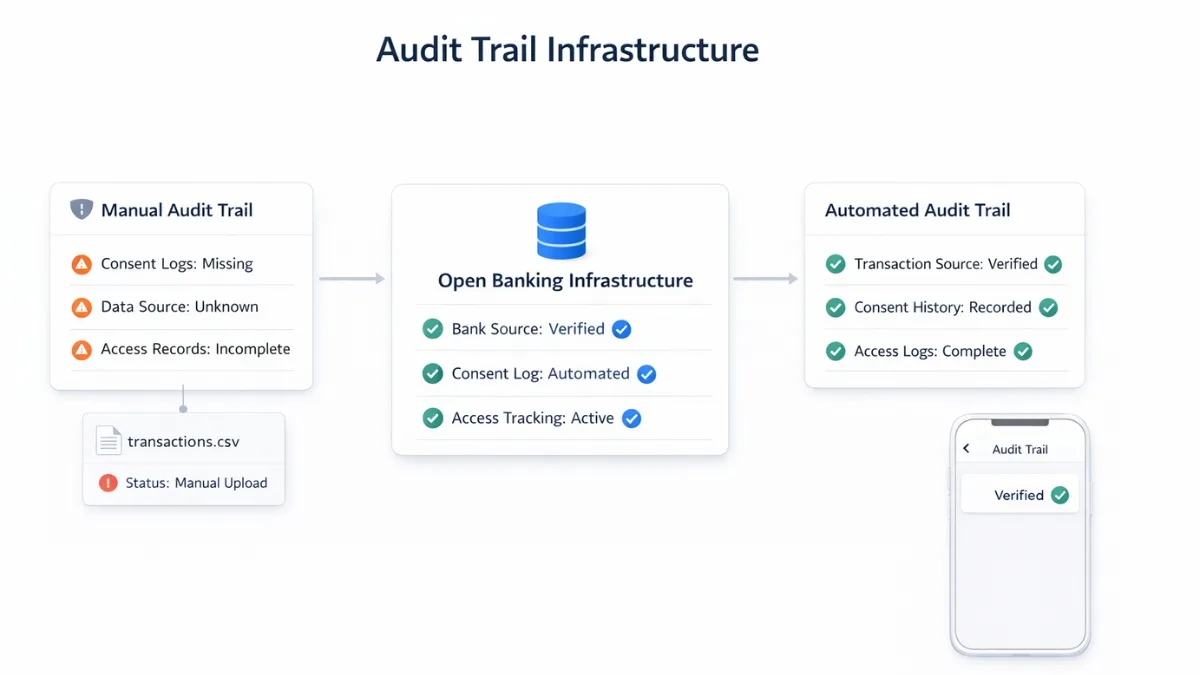
Manual Verification record creation introduces errors and delays. Bank-verified data infrastructure provides automated compliance records.
What breaks when using cheap providers?
Incomplete consent logs, missing transaction timestamps, and unreliable data provenance fail regulatory checks.
What should UK platforms prioritise?
FCA-authorised infrastructure that provides structured transaction data with verified bank sources and consent history.
Where does Finexer fit operationally?
Finexer handles bank connectivity and provides structured data. Platforms build compliance workflows and user interfaces on top.
Why do platforms struggle with audit trail records?
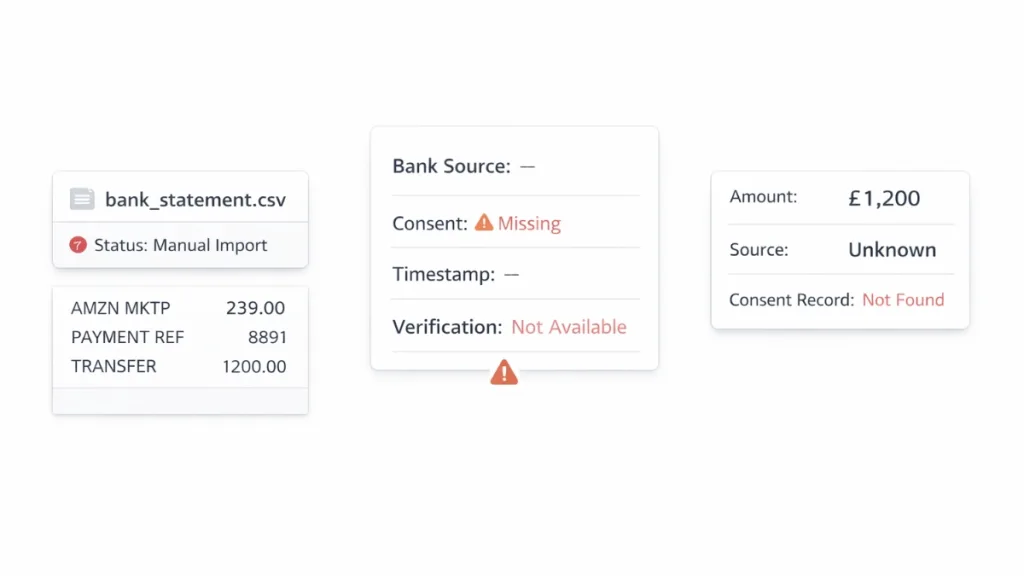
Most platforms access client bank accounts for reconciliation, verification, or payment processing. When audit trail records are incomplete, compliance teams cannot verify where data originated or when consent was granted.
This creates manual verification work. Finance teams must cross-check bank statements against platform records. Legal teams cannot confirm proper consent management.
Platforms using manual processes or CSV imports lack structured audit trail compliance. There is no verifiable record linking transactions to specific bank accounts or consent events.
According to the FCA’s guidance on data security, platforms processing client financial information must maintain clear audit trails showing how data was accessed and protected.
What happens when audit trail compliance fails?
Audit preparation becomes slow and expensive. Compliance teams spend days reconstructing data lineage for regulatory reviews.
Client onboarding delays increase. Platforms cannot quickly verify financial history when audit trail records are unclear or missing.
Regulatory risk increases. Platforms processing financial data without proper audit trail compliance face scrutiny during FCA reviews or client disputes.
Operational costs rise. Manual verification work requires additional staff time and slows down platform workflows.
What infrastructure prevents these failures?
Platforms need bank-verified transaction data with traceable origins. Each transaction must include metadata showing which bank account it came from and when consent was granted.
Consent lifecycle management must be automated. Platforms need timestamped records showing when clients authorised access, when consent expires, and when access was actually used.
Data must be structured and standardised. Audit trail records require consistent formatting across different banks and account types.
Real-time access logs must be maintained. Platforms need records showing when data was fetched, which API endpoints were used, and what information was accessed.
How does Finexer solve Verification record problems?
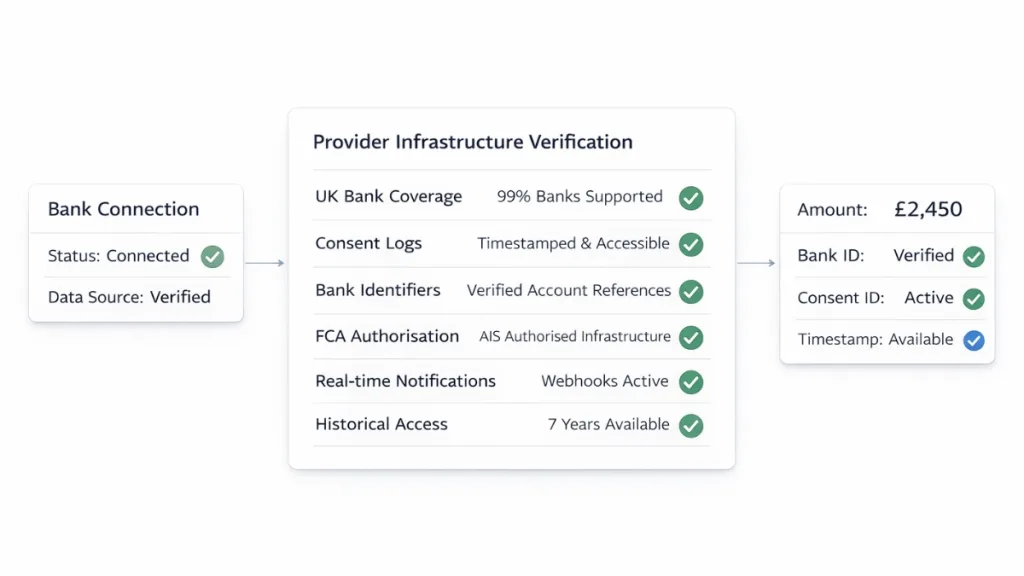
- Finexer provides FCA-authorised Open Banking infrastructure that connects platforms directly to UK banks, including Lloyds, Barclays, Monzo, Starling, and ~99% of UK banking providers.
- Bank transaction data includes verified provenance, with bank identifiers, account references, and structured metadata to support audit trail compliance.
- Consent management is handled within the infrastructure, with timestamped consent logs showing when access was granted, permissions provided, and consent expiry.
- Platforms receive real-time webhooks when new transactions occur, creating an automated audit trail of data access and trigger events.
- Historical transaction data access extends up to seven years (bank-dependent), allowing platforms to reconstruct complete audit records without manual entry.
- Integration support is provided during onboarding, while platforms remain responsible for building compliance workflows, user interfaces, and business logic on top of the infrastructure.
For platforms managing compliance verification processes, auditing with Open Banking integration provides additional context on regulatory requirements.
What should platforms check when evaluating providers?
Does the provider support all major UK banks and building societies? Incomplete coverage creates gaps in audit trail records.
Are consent events timestamped and accessible through APIs? Manual consent tracking introduces compliance risk.
Does transaction data include bank identifiers and account references? Generic data formats fail audit verification.
Is the provider FCA-authorised for Account Information Services? Unauthorised providers cannot legally access bank data.
Are real-time notifications available for new transactions? Delayed data access creates incomplete audit trail compliance.
Can platforms retrieve transaction history beyond 90 days? Short retention periods limit audit trail usefulness.
Platforms requiring verification infrastructure should confirm that bank data includes all necessary fields for compliance checks.
Common Infrastructure Mistakes
| Mistake | Why It Matters | What to Look For |
|---|---|---|
| Using CSV imports for audit trail | Manual uploads lack consent logs and data provenance | FCA-authorised API infrastructure with automated consent management |
| Relying on screen scraping | Data origin cannot be verified, fails regulatory checks | Direct bank connectivity through Open Banking standards |
| Choosing providers without webhook support | Platforms cannot track when data was accessed | Real-time notifications with timestamped access logs |
| Ignoring consent lifecycle management | Missing consent records create compliance gaps | Automated consent tracking with expiry management |
| Selecting providers with limited bank coverage | Audit trail records become incomplete for some clients | 99% UK bank coverage including challengers and building societies |
Platforms building Open Banking verification features should prioritise infrastructure that provides complete audit trail compliance automatically.
What I Feel
Most platforms underestimate the operational cost of maintaining proper audit trail records. Manual verification work scales poorly as client numbers increase.
The mistake I see most often is choosing infrastructure that provides transaction data without consent logs or access history. This creates compliance gaps that only become visible during regulatory reviews.
Cheap solutions that rely on screen scraping cannot provide verifiable Verification record compliance. When audit teams need to confirm data provenance during FCA reviews, platforms using unauthorised providers face serious risk.
Platforms serving regulated clients, such as those managing debt relief orders and IVAs, should treat audit trail infrastructure as a compliance requirement, not a technical feature.
The operational benefit comes from automation. Platforms that integrate proper infrastructure eliminate manual verification work and reduce compliance preparation time from days to hours.
What is an audit trail in financial platforms?
An audit trail is a record showing where financial data originated, when it was accessed, and who authorised the access. It provides verifiable documentation for compliance checks.
Why does audit trail compliance matter for UK platforms?
Platforms processing client financial data must demonstrate proper consent management and data provenance during regulatory reviews. Missing records create compliance risk.
Can platforms build audit trail infrastructure internally?
Platforms can build workflows and interfaces, but bank connectivity requires FCA authorisation. Most platforms use authorised infrastructure providers rather than applying for their own licenses.
How long should audit trail records be retained?
Retention requirements vary by use case. Most UK platforms retain records for six years to match accounting standards, though some regulatory requirements extend longer.
What makes Open Banking audit trail different from CSV imports?
Open Banking infrastructure provides bank-verified data with consent logs and timestamps. CSV imports lack data provenance and cannot demonstrate proper authorisation.
Get automated compliance records with bank-verified data.